About
SOTERIA Project
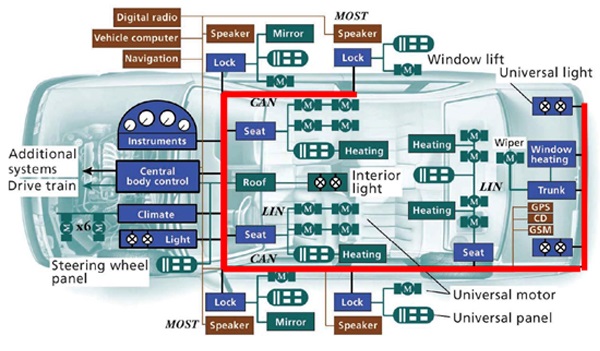
Cyber-enabled physical systems include all sorts of military vehicles (e.g. tanks, submarines, aircrafts)of the DoD that need to operate in adversarial environments during their mission. Since many of the military vehicles make use of the legacy hardware and protocols which did not anticipatable attacks on them, developing resilient algorithms and effectively incorporating into the existing legacy systems is one of the fertile areas of research. Our proposal addresses two main directions of research for CPS resiliency. We focus on the Controller Area Network (CAN) protocols.
Many of the DoD vehicles make use of variants of the Controller Area Network (CAN) protocols that were developed with a closed communication network in mind and did not have consider any aspect of security or protocol vulnerability. Even the civilian automotives, trucks and airplanes make use of the variants of CAN protocols that were developed with the assumption that the CAN was no accessible from external world. With the advent of modern Electronic Control Units (ECUs) that are capable of wireless communication, and the availability of the On-Board Diagnostics (OBD) ports, the CAN is no longer a closed network. Recent demonstrations of safety-critical remote attacks clearly show that the assumption of CAN being a closed network is very costly. We propose to address how to identify timing and voltage based covert channels that could be used to establish effective out of band communication among the ECUs for identification and/or authentication. We propose to investigate the resiliency of the recently proposed defense mechanisms against bus-off and voltage-based Intrusion Detection Systems.
Additionally, we propose to initiate the research into developing an analytical framework for the recently proposed BFT++ protocols of the ONR that goes beyond the Byzantine Fault Tolerance. While there is an initial boundary analysis based on inertia and delay, this area remains fertile and the notion of inertia in the context of cyber systems is yet to be uncovered.
Meet the Team
UW, Padua and Roma Tre Team

Prof. Radha Poovendran
Principal Investigator
Electrical & Computer Engineering, UW
Prof. Linda Bushnell
Co-Principal Investigator
Electrical & Computer Engineering, UW
Prof. Mauro Conti
Co-Principal Investigator
Department of Mathematics, University of Padua
Prof. Federica Pascucci
Co-Principal Investigator
Department of Engineering, University of Roma Tre
Surudhi Asokraj
Master's student, University of Washington
Tommaso Bianchi
Master's student, University of Padua
Claudio Stefani
Master's student, University of Padua
Federico Turrin
Ph.D student, University of Padua
Riccardo Colelli
Ph.D student, University of Roma Tre
Dinuka Sahabandu
Ph.D student, UW
Kalana Sahabandu
Masters student, UWPublications
Relevant Publications
S. Sagong, R. Poovendran, L. Bushnell, "Inter-Message Correlation for Intrusion Detection in Controller Area Networks", 2019 Conference on Embedded Security in Cars (ESCAR) Europe, Stuttgart, Germany, November 19-20, 2019
X. Ying, G. Bernieri, M. Conti, and R. Poovendran, "TACAN: Transmitter Authentication through Covert Channels in Controller Area Networks." In Proceedings of 10th ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Montreal, Canada, pp. 23-34, 2019.
X. Ying, S. Sagong, A. Clark, L. Bushnell, and R. Poovendran, "Shape of the Cloak: Formal Analysis of ClockSkew-Based Intrusion Detection System in Controller Area Networks”, IEEE Transactions on Information Forensics and Security, 14:9, pp. 2300-2314, January 2019.
S. Sagong, X. Ying, L. Bushnell, and R. Poovendran, “Exploring Attack Surfaces of Voltage-based Intrusion Detection Systems in Controller Area Networks”, in Embedded Security in Cars Europe, 2018.
S. Sagong, X. Ying, A. Clark, L. Bushnell, and R. Poovendran, “Cloaking the Clock: Emulating Clock Skew in Controller Area Networks”, in ACM/IEEE International Conference on Cyber-Physical Systems, 2018, pp. 32–42.
Universities
Participating Universities



Sponsor
Office of Naval Research

Network Security Lab @ UW | SPRITZ Group @ Padua | MCIP Lab @ Roma Tre
SOTERIA Project